SASE or SSE – That is the Question: Understanding Key Differences
- Kristopher Persad

- Aug 15, 2025
- 4 min read
To be SASE, or to be SSE? That’s the architectural dilemma facing today’s CIOs and CISOs.
In the rapidly shifting world of enterprise security, we’re no longer asking whether to modernize our security models — that ship has sailed. The real question is how to do it.
The Covid-19 pandemic didn’t just change where we work; it fundamentally reshaped how organizations think about connectivity and security. Practically overnight, companies that once operated almost entirely from physical offices had to enable a fully remote or hybrid workforce. The challenge wasn’t just keeping the lights on — it was doing so securely while employees accessed internal systems, cloud platforms, and external resources from everywhere.
Security vendors moved quickly, and with their solutions came a surge of industry buzzwords: Secure Access Service Edge (SASE), Security Service Edge (SSE), and Zero Trust. For many leaders, these terms became shorthand for the evolving strategies to safeguard a highly distributed workforce.

In this post, we’ll strip away the buzzwords and marketing hype to focus on what really matters:
What each term actually means.
The key differences.
How they fit into the Zero Trust framework.
By the end, you’ll have a clear, reference-backed understanding of SASE and SSE, and the confidence to answer the question: To be SASE, or to be SSE?
~ The SASE and SSE Uptick ~
Cloud adoption accelerated sharply — fuel for SASE/SSE. ESG/TechTarget found 85% of organizations accelerated cloud adoption because of the pandemic, with 94% using SaaS and/or IaaS and a notable rise in cloud-first strategies. TechTarget
SASE rose as the network/security answer to remote work. Early in the pandemic, enterprises raced to adopt SASE to reduce cost/complexity for a remote workforce. TechTarget
SSE crystallized as the security-only slice of SASE. Gartner formalized Security Service Edge (SSE) to secure access to web, SaaS, and private apps regardless of user/location—matching the remote/hybrid reality. Gartner
Zero Trust moved from concept to priority. McKinsey documented the pandemic’s acceleration of remote work and automation; parallel industry research shows organizations shifting from perimeter security toward Zero Trust to secure distributed access. McKinsey & Company | arXiv | ResearchGate
~ SASE v. SSE ~
Secure Access Service Edge (SASE) is a cloud-native architecture that integrates both an organization’s network (think SD-WAN) and security (think Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Zero Trust Network Access (ZTNA), Firewall as a Service (FWaaS)) into a single framework.
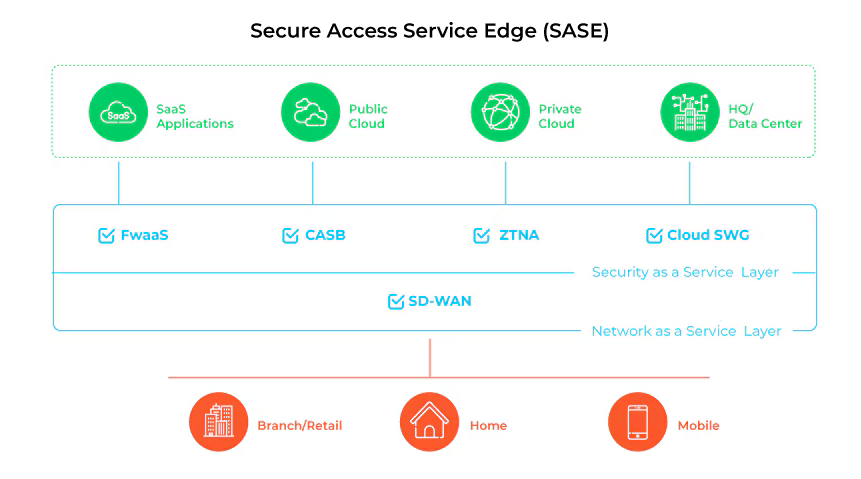
The goal: deliver secure, optimized access to applications and resources from anywhere, without relying on the traditional network edge or security perimeter.
Key traits of SASE:
Combines WAN capabilities and security controls into one platform.
Delivered primarily through cloud-based points of presence (PoPs) close to users.
Enforces policies based on identity, device posture, and real-time context.
Directly supports Zero Trust by ensuring no implicit trust, regardless of network location
Security Service Edge (SSE) is a cloud-delivered security architecture that focuses solely on the security components of SASE — namely Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Zero Trust Network Access (ZTNA). There is less of an emphasis on the network from the intended single or integrated solution.
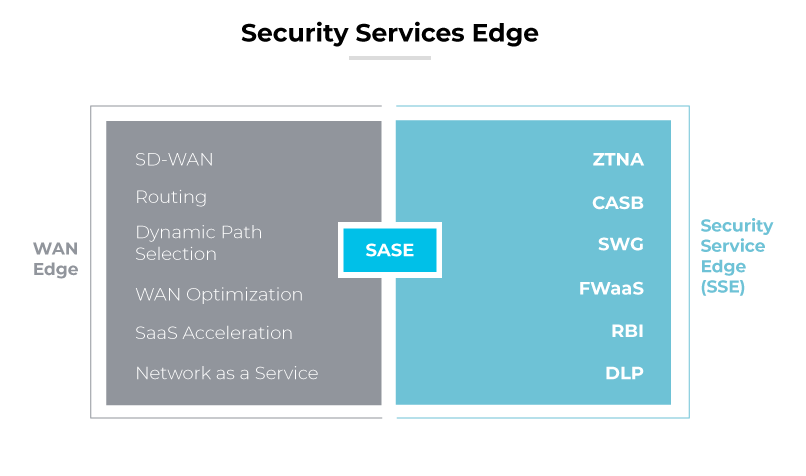
The goal: modernize and centralize security enforcement for users, devices, and applications, regardless of location, while allowing organizations to maintain their existing network infrastructure.
Key traits of SSE:
Provides a security-first approach without changing WAN routing or network architecture.
Protects users, applications, and data whether they’re on-premises, remote, or in the cloud.
Enforces Zero Trust principles by authenticating every user, device, and session.
Often adopted by organizations as a stepping stone toward full SASE implementation.
~ At a Glance ~
Feature/Scope | SASE | SSE |
Networking (SD-WAN) | ✅ | ❌ |
Security (SWG, CASB, ZTNA, FWaaS) | ✅ | ✅ |
Deployment Approach | Full network + security convergence | Security-first, network later |
Typical Use Case | Modernizing both WAN and security in one move | Modernizing security while keeping existing WAN |
Zero Trust Fit | Built-in | Built-in |
~ SASE & SSE in the Zero Trust context ~
SASE and SSE aren’t competitors — they’re two (2) architectural models that can both operate within the Zero Trust framework. As we established in our introductory post, Zero Trust isn’t a product, but a security philosophy and operational model built on the principle of “never trust, always verify”.
Where SASE combines networking + security into a unified, cloud-delivered architecture, SSE focuses exclusively on the security stack. Both enforce Zero Trust principles by validating every user, device, and session, applying contextual access controls, and reducing the attack surface.
Zero Trust serves as the overarching security governance framework, shaping the operational behaviours and policies that make SSE or SASE effective in practice.
In a SASE model, Zero Trust principles extend from the network layer all the way to application access, creating end-to-end protection.
In an SSE model, Zero Trust principles focus on securing access to apps, data, and services, even if the network transport remains unchanged.
Think of SASE and SSE as vehicles, and Zero Trust as the traffic laws and driving philosophy that ensure both vehicles reach their destination safely — no matter which route you take.
References: Palo Alto Networks: SASE vs. SSE: What Is the Difference? | Gartner – What Is SASE? | Gartner – What Is SSE? | Cloudflare – SASE vs SSE | Cisco – SSE Explained
Image References: Palo Alto Networks



Comments